Time to Upgrade: Why We Must Replace ISIS Now
I have been a UC San Diego employee since 2016, and I can still vividly remember the day that I was introduced to the university’s Integrated Student Information System (ISIS). I was being trained in my new role as a Program Manager for Extended Studies, and the first time I saw ISIS, I felt that I was transported back in time 30 years–I honestly expected to hear some dial-up internet sounds to accompany the black and green screen interface.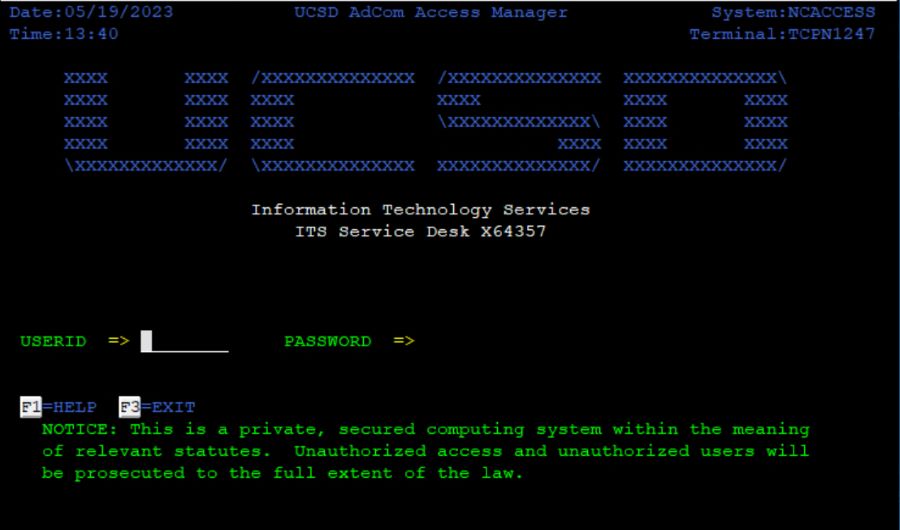 Needless to say, I was shocked and surprised that UC San Diego, a world-renowned university and research institution, was using a system that felt and looked so antiquated. If you have ever worked directly in ISIS, I would guess that perhaps you had similar feelings upon your first encounter.
Needless to say, I was shocked and surprised that UC San Diego, a world-renowned university and research institution, was using a system that felt and looked so antiquated. If you have ever worked directly in ISIS, I would guess that perhaps you had similar feelings upon your first encounter.
While ISIS is a system that was state of the art for its time and has served the university well since the late 1980s, both the needs of UC San Diego and technology in general have drastically changed since its inception. To delve into the world of ISIS further, I met with Jonathan Whitman (Senior Director, Student Information Services, IT Services) and David Hutches (Enterprise Architect, IT Services) to learn more about ISIS and why the university is working so hard to replace it.
The Limitations of ISIS
Most UC San Diego employees likely do not interact with the ISIS mainframe (the so called “green screens”) on a regular basis, but many do regularly use the data that comes from ISIS. When I asked Jonathan and David to identify just two or three of the challenges of working with ISIS, they each listed more than five, proving that the use of ISIS is a continued risk to the university and its operations.
David shared that ISIS “becomes increasingly difficult and expensive to enhance or even maintain its functionality…[and] because of [its] limitations, [it has] led us to build a complex ecosystem of supporting infrastructure around the core capabilities.” The impact of this workaround and customization approach means that students, faculty and staff must use multiple systems, methods and external resources to accomplish what should be basic tasks or functions. From my personal experience as a staff member, I recall feeling frustration on a weekly basis because of inefficient use of my time needing to do double entry and developing creative solutions to do rudimentary work that I thought a system should be capable of doing.
Jonathan adds to this saying, “Over the last 20 years, we’ve developed a lot of applications around ISIS to meet the demands of our staff and students in the age of the internet.” Having applications of varying ages and in varying states of technology takes an increasing amount of time and effort to update and keep them in compliance with present-day cybersecurity standards.
With the recent rise in cybersecurity attacks and the increased risk of data theft, it is paramount that we know the university is not only protecting our personal information and valuable research, but is able to respond swiftly and efficiently to potential threats or attacks. In order for this to be a reality, we need a modern, unified system.
The Frankenstein Way
To echo David’s statement, ISIS has several limitations that prevent it from being able to fully serve the current needs of the university. As a basic example, the system is running out of numerals to create section identification numbers (section IDs). The system simply was not conceived to be running this long, and therefore the creators did not account for more than a million section IDs. Imagine what would happen if we did reach a point where we could not create any new section IDs. The university would not be able to function effectively because section IDs are at the center of many necessary operations, such as creating a class, course enrollments, student payments, faculty assignments, and more.
For a more complex but no less critical example, ISIS does not currently have the capability to integrate lived name functionality, which is a presidential policy from President Michael V. Drake, M.D. As Jonathan puts it, continuing to use ISIS in its current state means that “we have to engineer a way to make adjustments outside of the system and then integrate it back into the system.” A process that is messy and takes copious amounts of time and resources.
David adds, “The complexity of our institutional needs and those of the state, national and global environment in which we operate has increased dramatically since ISIS was first designed and built. It is a disservice to our students and our instructional mission not to have a system that better meets those needs.”
Lastly, the absence of ISIS legacy knowledge is also a perpetuating challenge that Jonathan expressed. Because ISIS was engineered over thirty years ago, there are no longer any staff around who truly and deeply understand its inner workings. In order to answer intricate engineering or historical-knowledge questions, the incredibly talented staff in IT Services have to “spend hours reverse engineering the code to try to understand it.” Therefore, staff time, resources and talent are being utilized to keep an old system afloat rather than being utilized for more crucial efforts that could have a more direct impact to the daily needs of students, staff and faculty.
Time for a Trade In
As I keep talking with Jonathan and David, it becomes more clear to me that we simply cannot continue operating on ISIS. Although I held separate interviews with each of them, both compared the use of ISIS to having an antique car, where it takes specialized legacy knowledge and parts in order to run it, making it increasingly expensive and challenging to maintain. I completely resonate with the imagery that David painted for me: “If you have a classic car and you restore it and keep it going, it might be cool to take it out for a Sunday drive, but it is not going to be your daily commuter car because you know how fragile it is.”
The Impacts of Replacing ISIS
While there is no denying the challenges with ISIS, we must also acknowledge the incredible impact that adopting a new student information system will have on the university. Just like with every change, there are two sides to this coin. “Ultimately, there will be many positive impacts such as more timely and detailed access to data that ultimately improve both student experience and success. Additionally, there will be marked improvement in the effectiveness and efficiency of our operations,” David says.
With that, however, we also have the opportunistic impacts–those impacts that are less than ideal, but that give us a chance to reassess and revise our current practices and experiences. One exceptional opportunity is in reevaluating our business processes and how we think about and complete our day-to-day work.
We have grown accustomed to working within a system that has limitations and quirks, where we have had to constantly find workarounds to accomplish basic tasks or projects. Implementing a new SIS has challenged us (and will continue to challenge us) to separate our business processes from the databases and systems we use to complete them–understanding the what and the why of our business operations rather than the how.
This mental shift is a big ask. When I think back to my position as a Program Manager, almost every process or task that I did was connected to a system, and I thought about them as one in the same: I need to do X, so I go to Y database. The shift here instead is thinking about our processes as system agnostic, as not deeply grounded in a system. As David so easily explained it, “The technology is not the work–it's the tool that helps us to do our work.”
I would argue that this mindset is a transformational change–a large cultural change of how the university has been operating and thinking for the past decades. Many of our job identities are intricately connected to the systems that we use, and we honestly couldn’t even fathom doing our job without those systems. However, with a new SIS, we will have to take on that new perspective in order to enable effective adoption, minimize impact and ensure continued successful operations.
What’s It All For Anyway
The SIS Project team has been diligently working for the last four years on the replacement of ISIS, and it is anticipated that the project will continue for another few years. Even though the team has put in an incredible amount of hours and work into the project, they still remain hopeful about the outcome and the impact to the university.
“I’m most excited about giving our students an experience that matches that of the world-class university we are,” Jonathan says.
“This is a once in a lifetime opportunity,” David emphatically claims, “for genuine customer engagement that will help us, IT Services, to facilitate the most effective use of technology that we have” to help ease the pain points for students, staff and faculty.
In their final statements, both Jonathan and David place the emphasis on the student experience, showcasing that the collective effort and driving force of the SIS Project to replace ISIS is the same now as when the project first started–to demonstrate that we are a student-centered university and seek to improve the overall student experience.
Learn more about the SIS project at esr.ucsd.edu/student.
For questions about the SIS project contact esr-student@ucsd.edu.